NMap (Network Mapper) is a powerful open-source tool for network exploration and security auditing. It can be used to discover hosts and services on a computer network, thus creating a “map” of the network. Some of the common tasks NMap can perform include:
1. Host discovery: Identifying hosts on a network.
2. Port scanning: Listing the open ports on a target host.
3. Service enumeration: Identifying the services (including versions) running on open ports.
4. OS detection: Determining the operating system and hardware characteristics of network devices.
5. Vulnerability scanning: Detecting potential vulnerabilities in network services.
Steps to Find Network Vulnerabilities Using NMap
1. Install NMap
Ensure NMap is installed on your system. You can download it from the official NMap website or install it via a package manager. For example, on a Debian-based system, you can install it with: sudo apt-get install nmap
sudo apt-get install nmap

2. Basic Host Discovery
To identify live hosts on a network:
nmap -sn 192.168.1.0/24

This command will ping the subnet `192.168.1.0/24` to discover active hosts.
3. Port Scanning
To list open ports on a specific host:
nmap 192.168.1.1

4. Service Enumeration
To identify services and their versions running on open ports:
nmap -sV 192.168.1.1

5. Operating System Detection
To determine the operating system of the target host:
nmap -O 192.168.1.1

6. Vulnerability Scanning
NMap has a scripting engine (NSE) which includes scripts for vulnerability detection. For example, to run a vulnerability scan:
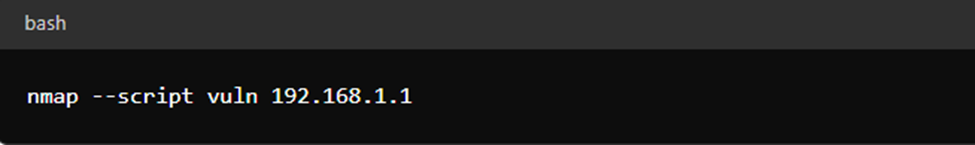
nmap –script vuln 192.168.1.1
Example: Comprehensive Scan
nmap -A -T4 192.168.1.1
For a thorough scan combining several techniques, you can use:

This command includes OS detection, version detection, script scanning, and traceroute.
Common Vulnerability Scripts
NMap’s scripting engine (NSE) includes many scripts for detecting various vulnerabilities. Here are some examples:
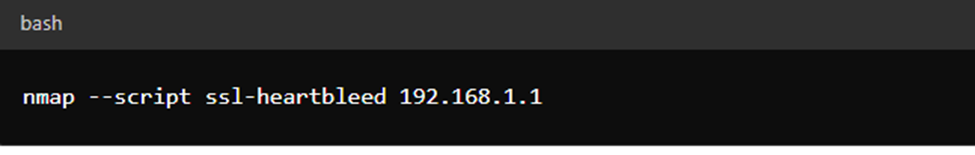
1. Heartbleed
nmap –script ssl-heartbleed 192.168.1.1
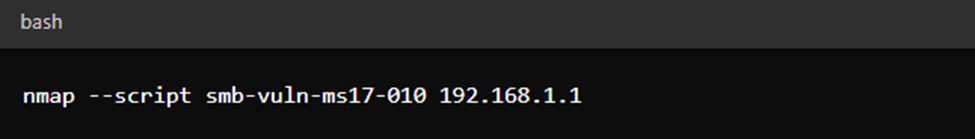
2. SMB Vulnerabilities (e.g., MS17-010)
nmap –script smb-vuln-ms17-010 192.168.1.1
3. HTTP Vulnerabilities
nmap –script http-vuln-cve2017-5638 192.168.1.1
Running a Full Vulnerability Scan
To run a comprehensive vulnerability scan using all available vulnerability scripts:
nmap –script vuln 192.168.1.1

Interpreting Results
After running these scans, NMap will provide output detailing:
– Open ports and the services running on them
– OS and version detection
– Potential vulnerabilities and weaknesses
Carefully analyze these results to identify and mitigate potential security issues in your network. Always ensure you have authorization to scan the networks you are analyzing to avoid legal and ethical issues.



