A VPN (Virtual Private Network) is a technique used to secure communication between two network devices. VPNs are used to facilitate privacy and security whenever information travels across public networks such as the Internet. VPNs can also be used to hide public-facing IP addresses and for extending private networks over public networks. With the help of VPN, it is possible to hide online activities such as the websites visited, and the files downloaded. VPNs leverage tunneling protocols and encryption algorithms such as OpenVPN (on open-source VPN protocol) and AES (Advanced Encryption Standard) algorithms.
There are different approaches that can be used to configure VPN on Kali Linux. There are companies that offer paid VPN services, but there are also free VPN services. In this article, we will focus on installing and enabling free OpenVPN on Kali Linux. We will follow the below steps to download and install OpenVPN on our Kali Linux machine.
Step 1
Open your web browser, navigate to Google and search for free vpnbook openvpn then press enter.
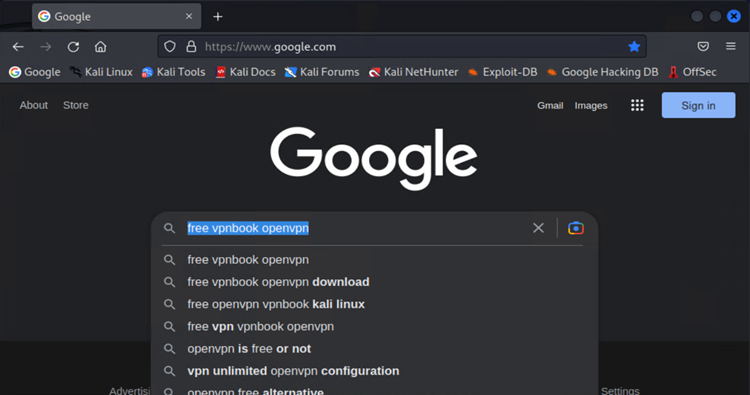
Step 2
On the results list that is generated, click on the link that takes you to vpnbook.com
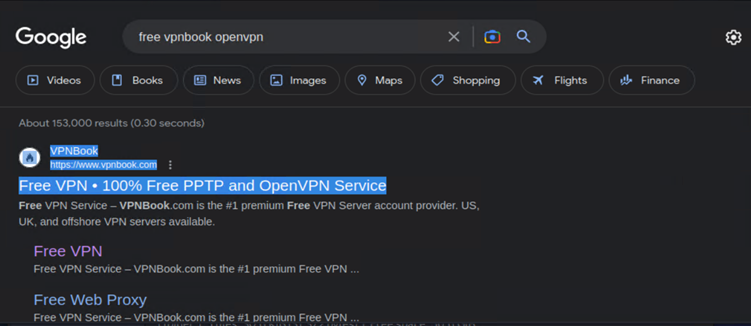
Step 3
Once on the vpnbook.com site, scroll down to the section that reads “Free OpenVPN and PPTP VPN” and click on the OpenVPN tab. A list of available profiles will be listed. Select a certificate bundle that you would like to try and the download process will start.
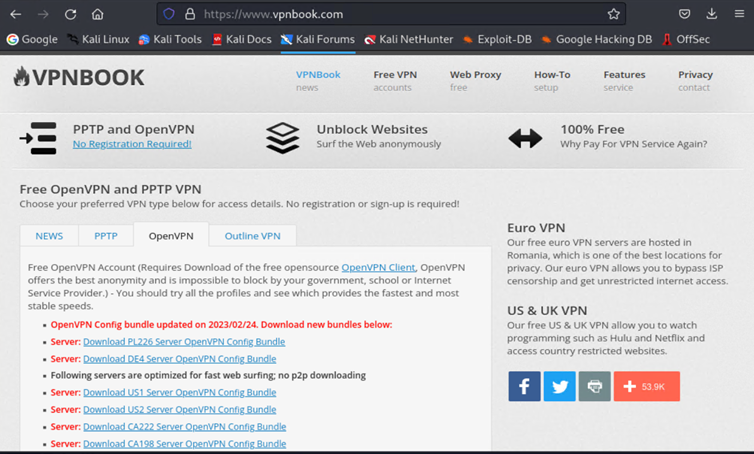
Note: You will need the username and password for that OpenVPN certificate bundle. This is information is listed toward the bottom of the list of the available VNP certificate bundles.
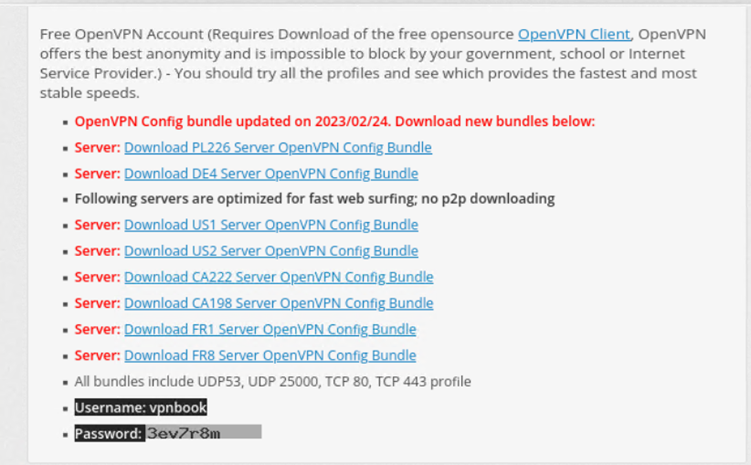
Step 4
Navigate to the directory in your folder where the file was downloaded to (by default this should be the Downloads folder).
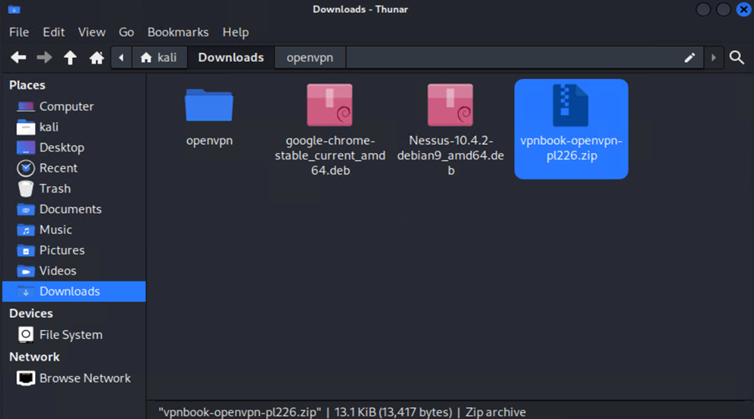
The next step is to unzip the downloaded file. There are two ways to do this. The first way is through the GUI (open file system > find folder that contains file > right click on the file and select one of the Extract options).
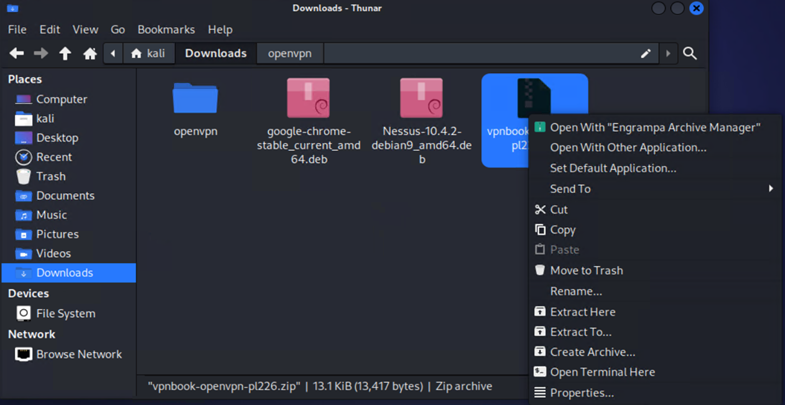
The second way is through the terminal. Navigate to the directory that contains the downloaded file and use the below command:
unzip <name of the zipped file>
Example:
unzip vpnbook-openvpn-pl226.zip
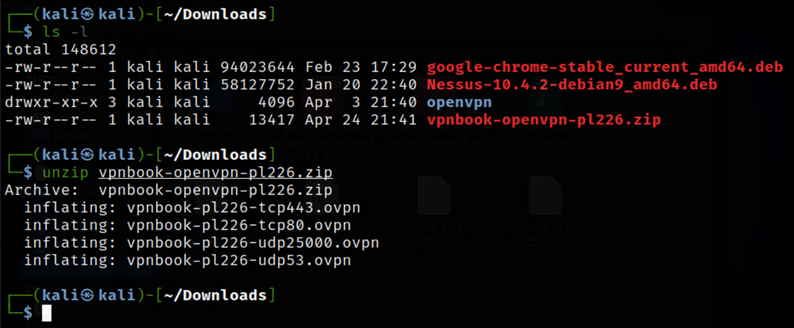
Step 5
Open/enable the OpenVPN using the below command:
sudo openvpn <name of one of the extracted files>
Example:
sudo openvpn vpnbook-pl226-tc.80.opvn
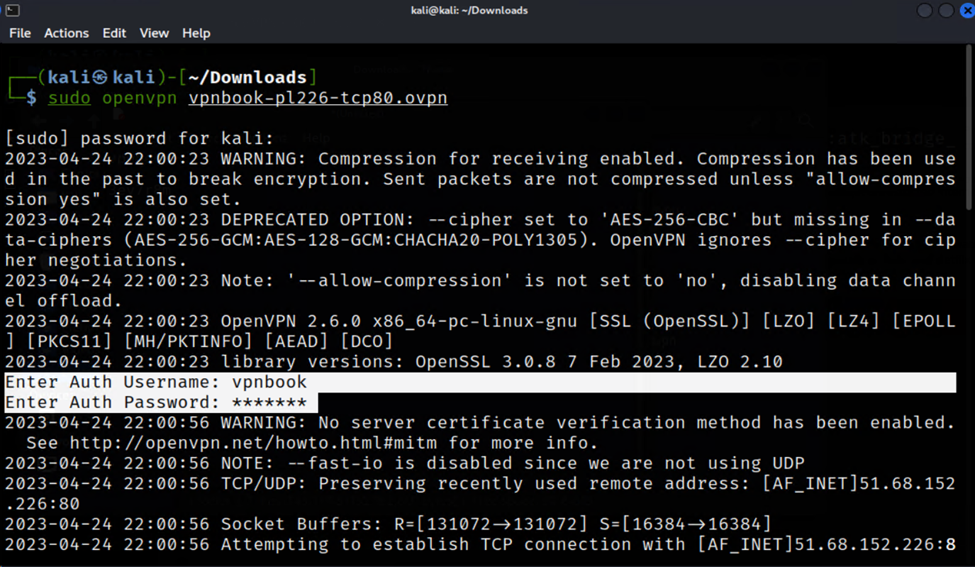
Step 6
Enter the username and password obtained in Step 3.
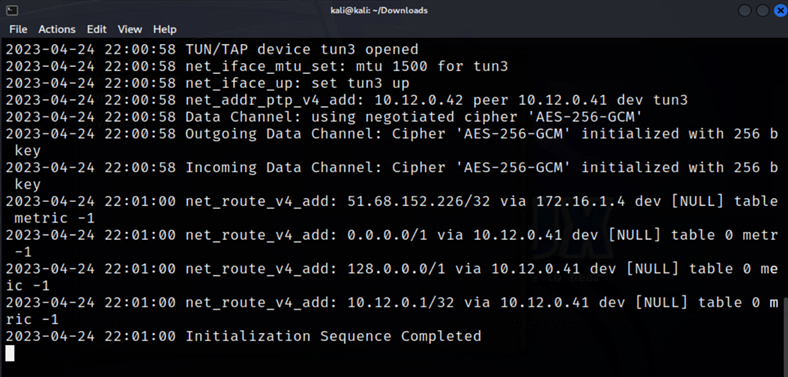
Step 7
Once cipher and other tunnel settings are successfully completed, you will get a message that reads “Initialization Sequence Completed”. This message confirms that the VPN has been enabled.
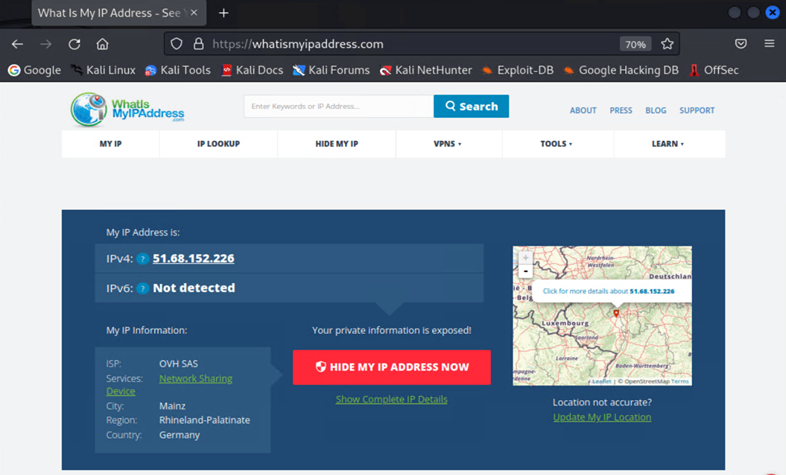
You can now open a browser and check your public IP address by searching for “what is my ip” or “ip chicken.” The public IP address that is displayed should be different from your actual public IP address.
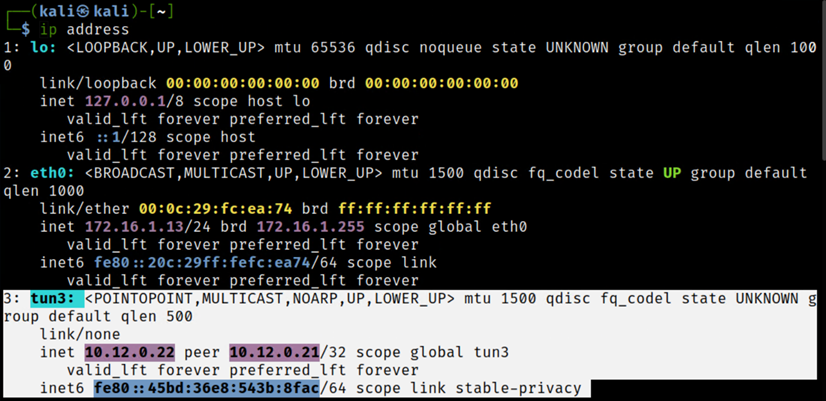
When your VPN is enabled, your online communications will be routed through the tunnel created between your device and the VPN provider/server. We can also view the newly created tunnel interface by running the following command at the terminal:
ip address
Conclusion
In this article, we gave an overview of what a VPN (Virtual Private Network) is and what it can be used for. We provided a step-by-step demonstration of where to locate, download and enable a free VPN on a Kali Linux machine. This free open-source VPN protocol is also referred to as OpenVPN. Finally, we showed how to check and verify the Kali Linux machine’s public IP address once we have enabled VPN.



